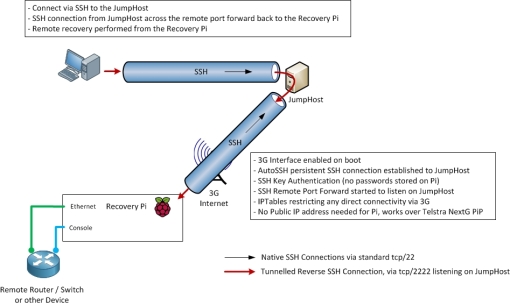
My previous single Raspberry Pi posts have been steps towards my “Recovery Pi”
a small self sufficient system that can be shipped to
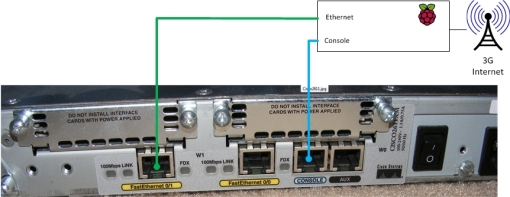
a remote site to facilitate serial (console) & network
(mgmt lan) connectivity to the remote devices
• Raspberry Pi ($45)
– http://www.raspberrypi.org/faqs
• USB->Serial Convertor ($30)
– http://www.jaycar.com.au/productView.asp?ID=XC4834
• Cisco Console Cable
• Telstra 3G “Elite” USB Modem ($29)
– http://www.telstra.com.au/internet/mobile-broadband-prepaid/get-started/#tab-elite-usb
– Telstra AUS Mobile Internet $180/year (365 day access | 1.46c per MB in AUS | $15.36 per MB Intl Roaming)
• 8GB SDHC Mem Card ($10)
• USB Power Brick (~10hrs run) ($20)
– http://www.tevion-cameras.com/popups/MPP_7400_au_popup_02/
• USB Powered Hub ($18)
– http://hakshop.myshopify.com/products/usb-powered-hub
• Total Retail Startup Cost: $152 AUD
===Built on the existing Debian Squeeze image===
http://downloads.raspberrypi.org/images/debian/6/debian6-19-04-2012/debian6-19-04-2012.zip
===Telstra 3G USB Modem===
root@raspberrypi:~# apt-get install usb-modeswitch pppd
root@raspberrypi:~# dmesg | grep ttyUSB
usb 1-1.2.4: GSM modem (1-port) converter now attached to ttyUSB0
usb 1-1.2.4: GSM modem (1-port) converter now attached to ttyUSB1
usb 1-1.2.4: GSM modem (1-port) converter now attached to ttyUSB2
usb 1-1.2.3: pl2303 converter now attached to ttyUSB3
root@raspberrypi:~# cat /etc/chatscripts/telstra
ABORT ‘NO CARRIER’
ABORT ‘NO DIALTONE’
ABORT ‘BUSY’
ABORT ‘ERROR’
ABORT ‘NO ANSWER’
” ‘ATZ’
OK ‘AT&F’
OK ‘ATQ0 V1 E1′
OK ‘AT&D2 &C1′
OK ‘AT+FCLASS=0′
OK ‘ATS0=0′
OK ‘AT+CGDCONT=1,”IP”,”telstra.internet”‘
OK ‘ATDT*99#’
CONNECT ”
root@raspberrypi:~# cat /etc/ppp/peers/telstra
/dev/ttyUSB2
460800
modem
crtscts
defaultroute
noipdefault
usepeerdns
ktune
noauth
lock
nobsdcomp
novj
connect “/usr/sbin/chat -v -f /chatscripts/telstra”
root@raspberrypi:~# pon
root@raspberrypi:~# ifconfig ppp0
ppp0 Link encap:Point-to-Point Protocol
inet addr:10.138.162.113 P-t-P:10.64.64.64 Mask:255.255.255.255
UP POINTOPOINT RUNNING NOARP PROMISC MULTICAST MTU:1500 Metric:1
RX packets:705 errors:0 dropped:0 overruns:0 frame:0
TX packets:624 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:3
RX bytes:621353 (606.7 KiB) TX bytes:40301 (39.3 KiB)
root@raspberrypi:~# poff
===3G Connection On Boot===
root@raspberrypi:~# cat /etc/network/interfaces
# Used by ifup(8) and ifdown(8). See the interfaces(5) manpage or
# /usr/share/doc/ifupdown/examples for more information.
auto lo
iface lo inet loopback
auto ppp0
iface ppp0 inet ppp
provider telstra
===Reverse SSH Connection & AutoSSH===
root@raspberrypi:~# ssh-keygen
root@raspberrypi:~# ssh-copy-id recoverypi@jumphost
-Manual-
root@raspberrypi:~# ssh -R 2222:localhost:22 recoverypi@jumphost
-Auto-
root@raspberrypi:~# apt-get install autossh
root@raspberrypi:~# autossh -M 20000 -f -N -R 2222:localhost:22 recoverypi@jumphost -i /root/.ssh/id_rsa
Add the command into /etc/rc.local before the “exit 0” line & you are good to go on every reboot.
autossh -M 20000 -f -N -R 2222:localhost:22 recoverypi@jumphost -i /root/.ssh/id_rsa
– Connect to your JumpBox & verify the Pi has “phoned home”
recoverypi@jumpbox:~$ netstat -ant | grep 2222
tcp 0 0 127.0.0.1:2222 0.0.0.0:* LISTEN
tcp6 0 0 ::1:2222 :::* LISTEN
– Connect across the reverse SSH tunnel to the Pi
recoverypi@jumpbox:~$ ssh root@127.0.0.1 -p 2222
root@127.0.0.1’s password:
Linux raspberrypi 3.1.9+ #84 Fri Apr 13 12:27:52 BST 2012 armv6l
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Tue Jul 17 22:27:42 2012 from raspberrypi
root@raspberrypi:~#
===MINICOM===
root@raspberrypi:~# apt-get install minicom
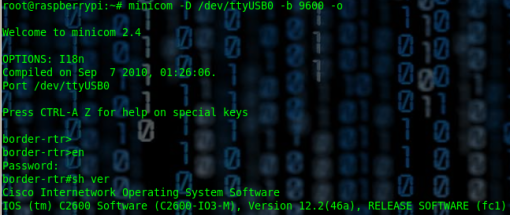
root@raspberrypi:~# minicom -D /dev/ttyUSB3 -b 9600 -o
Welcome to minicom 2.4
OPTIONS: I18n
Compiled on Sep 7 2010, 01:26:06.
Port /dev/ttyUSB3
Press CTRL-A Z for help on special keys
border-rtr>
border-rtr>en
Password:
border-rtr#sh ver
Cisco Internetwork Operating System Software
IOS ™ C2600 Software (C2600-IO3-M), Version 12.2(46a), RELEASE SOFTWARE (fc1)
===TFTP===
root@raspberrypi:~# apt-get install xinetd tftpd tftp
root@raspberrypi:~# vi /etc/xinetd.d/tftp
————————————-
service tftp
{
protocol = udp
port = 69
socket_type = dgram
wait = yes
user = nobody
server = /usr/sbin/in.tftpd
server_args = /tftpboot
disable = no
}
————————————-
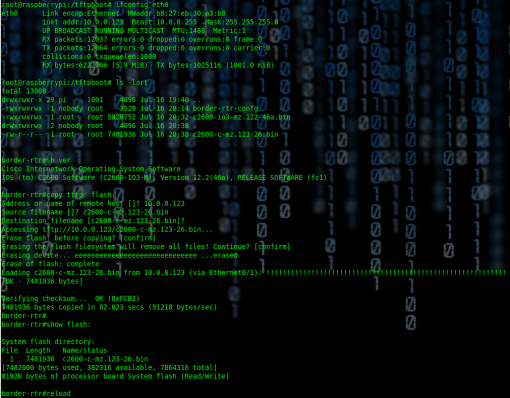
root@raspberrypi:~# mkdir /tftpboot
root@raspberrypi:~# chmod -R 777 /tftpboot
root@raspberrypi:~# chown -R nobody /tftpboot
root@raspberrypi:~# /etc/init.d/xinetd stop
Stopping internet superserver: xinetd.
root@raspberrypi:~# /etc/init.d/xinetd start
Starting internet superserver: xinetd.
root@raspberrypi:~#